Mrs. King - School Year 2010-2011
Wednesday, September 23, 2020
Tuesday, September 22, 2020
Twelve Years Later...
Twelve years ago, I rediscovered the joy of simple, old school gaming through a rules-light d20 clone called "microlight20".
A gent by the name of Greywulf was very active in this space and he'd started the old site microlite20.net. It had a blogging feature and my very first oldschool related post was on May 12th:
https://web.archive.org/web/20100611221707/http://microlite20.net/blog?page=5
Anyway, my search for a fun D&D game to play had rekindled in late 2007, early 2008 when I sat down with a borrowed copy of the D&D 3.5 rules and tried to scratch out a campaign for Ultima. After needing spreadsheets and a writeup that felt like a movie script, I realized that I wanted to go back to the days of when D&D (to me) was simple and fun. Thus, I wound a crazy road through microlite20, then through Swords & Wizardry and OSRIC, finally coming back to just playing the originals now that they were commercially available again.
What a fun journey.
Participating in an RPG does something to the brain, I think. There's an imprint that happens.
If you've read Dragonriders of Pern, (spoilers for those who haven't), I think of it similar to how someone imprints on a dragon during Hatching. You discover the game that speaks to you, and it's a match that will never ever quite go away. It's a first love. With all the ignoring of the warts and issues. The first time of escaping your life and living vicariously through the life of a made up character - or as a deity of a made up world. It something that I think has a profound effect on us, especially when we encounter the concept and play as a child. Impression.
For me, that impression was with Holmes (which was, IMO, OD&D levels 1 - 3) and AD&D. I've played other games, I can appreciate other games, but I will always be imprinted with those originals.
I made a list of the things I've written, been involved in or contributed to during these past twelve years and it's told me one thing... I'm part of a special group of players who imprinted much like I did. We're a raucous bunch, opinionated and crotchety about our games, but at the core, I suspect there's a feeling of wonder and joy, much like that first time we picked up those dice and stepped into another world. We love to create, to share and to experience the game again and again.
Happy Anniversary, y'all. I'm really glad I discovered our niche of a niche. I'm here to stay.
A gent by the name of Greywulf was very active in this space and he'd started the old site microlite20.net. It had a blogging feature and my very first oldschool related post was on May 12th:
https://web.archive.org/web/20100611221707/http://microlite20.net/blog?page=5
Howdy!Submitted by chgowiz on Mon, 05/12/2008 - 13:26Oh, another blog. Yay! :)Heh. Even back then, if a programming or hacking challenge raised its ugly head, I would jump in feet first. That's how I got involved in the One Page Dungeon Template thing...
My "old" blog is at http://chgowiz.livejournal.com - it's full of other 'stuff', not related to gaming and D20 or m20.
Coming soon to this site, however... the m20 character generator! A basic 'core' version was scratched out this weekend, but now I'm working on a 'better' version that will include Macropedia rulesets.
More to come as Greywulf gets this site up and running...
Links
Anyway, my search for a fun D&D game to play had rekindled in late 2007, early 2008 when I sat down with a borrowed copy of the D&D 3.5 rules and tried to scratch out a campaign for Ultima. After needing spreadsheets and a writeup that felt like a movie script, I realized that I wanted to go back to the days of when D&D (to me) was simple and fun. Thus, I wound a crazy road through microlite20, then through Swords & Wizardry and OSRIC, finally coming back to just playing the originals now that they were commercially available again.
What a fun journey.
Participating in an RPG does something to the brain, I think. There's an imprint that happens.
If you've read Dragonriders of Pern, (spoilers for those who haven't), I think of it similar to how someone imprints on a dragon during Hatching. You discover the game that speaks to you, and it's a match that will never ever quite go away. It's a first love. With all the ignoring of the warts and issues. The first time of escaping your life and living vicariously through the life of a made up character - or as a deity of a made up world. It something that I think has a profound effect on us, especially when we encounter the concept and play as a child. Impression.
For me, that impression was with Holmes (which was, IMO, OD&D levels 1 - 3) and AD&D. I've played other games, I can appreciate other games, but I will always be imprinted with those originals.
I made a list of the things I've written, been involved in or contributed to during these past twelve years and it's told me one thing... I'm part of a special group of players who imprinted much like I did. We're a raucous bunch, opinionated and crotchety about our games, but at the core, I suspect there's a feeling of wonder and joy, much like that first time we picked up those dice and stepped into another world. We love to create, to share and to experience the game again and again.
Happy Anniversary, y'all. I'm really glad I discovered our niche of a niche. I'm here to stay.
Saturday, September 12, 2020
Download Charectar Replace Mod For Gta Sandea
This mod is only for gta sandeas
to control this mod read discription
discription
CHARECTOR MOD
TO GO FRANKLIN PRESS=ALT+UP ARROW KEY (AND ALT+F10)
TO GO MICHELL PRESS=ALT+RIGHT ARROW KEY (AND ALT+F9)
TO GO TREVOUR PRESS+ALT+RIGHT ARROW KEY(AND ALT+F12)
PHONE MOD
TO BBRING YOUR CALL PRESS= TAB AND ENTER KEY
TO USE YOUR PHONE PRESS=ALT+P OR SHIFT+P KEY
TO UNLOCK YOUR PHONE PRESS SHIFTE KEY
TO BACK YOR PHONE PRESS RIGHT ARROW KEY
USE MORE FUNCTION TO THIS SO PLESE RED ME FILE ON THIS MOD
MOD DISCRIPTION
THIS MOD CAN CHANGE ALL MAP AN PHONE AND CHARCTOR SKINS PLAYER
IT COULD NOT CHANGE YOU GRAPHIC AND MISSON OF GTA SNADEAS IT COULD USE
IN MINNIMUM 2GB RAM AND 500 GRAPHIC CRAD SO REMEMBER ALL NOTES TO US\E MORE FUNCTION OF THIS MOD SO PLESE DOWNOAD AND READ README FILE
TO USE THIS MOD
DOWNLOAD WINRAR LATEST UPDATE SOFTAWRETO USE THIS MOD DOWNLOAD IT FROM HERE
GET FREE WIN RAR SOFTWARE
mod password is=fulla1
DOWNLOAD THIS MOD FROM HERECreative Gaming Watch: Divinity: Original Sin 2
A rare non-Storium post here, but even if that has largely taken over the blog, I do still keep an eye on other forms of creative gaming!
One concept I've always been interested in is a game which merges, as much as possible, the ease of play of a video game and the creative power of a tabletop RPG. Not just a virtual tabletop, but something that actually played like a video game, but allowed someone to create and run their own adventures. There have been some attempts throughout the years - Neverwinter Nights, for instance, was a good shot at it, and Sword Coast Legends was a recent...not-quite-as-good shot at it. But nothing's quite gotten there for me - either there was too high of a barrier to entry for the GM for my tastes, or things were easier for the GM but fairly limited in power.
Obviously, that's quite a balancing act. But, fortunately, it hasn't stopped game companies from trying...and that brings me to today's subject, Divinity: Original Sin 2.
The first Divinity: Original Sin is quite a nice game, full of tabletop flavor and with an impressive amount of freedom for a video game - there are constraints, as one would expect since nobody can program for everything, but it definitely feels like you have more approaches to situations than in many other video game RPGs. I've found this particularly interesting in combat, where there seem to be all sorts of interesting tactical options that I can try to take advantage of and usually end up accidentally shocking and stunning my own guy, because I suck at tactical gameplay. The system's pretty brilliant, I'm less so.
Divinity: Original Sin 2 is building on that and adding new tactical options, and expanding the rest of the game besides...but it's also doing one more thing that has me very excited. It's adding a GM mode.
Like the mode in Sword Coast Legends, it appears this one is focused more on the concept of live GMing, rather than building a plot that can be played without a GM like Neverwinter Nights allowed. Not sure if that will be an option too or not. Regardless, the live GMing mode looks very promising in the previews I've seen so far. A few highlights:
I'm less enthused by the character creation engine...specifically, for appearance. There's just not that many options at this point for those of us who really get into appearance creation, and I honestly don't know why games based on tabletop roleplaying don't ever go whole hog with character appearance creation the way things like Dynasty Warriors 8: Empires or Dragon's Dogma do, to say nothing of various WWE 2k wrestling games or the like. If any game type should let you truly put the character in your mind on to the screen, it's one with a strong tabletop gaming concept like this, but it never really happens. Here's hoping that they take another look at this at some point, but it seems pretty locked in now. Ah, well. If this GM mode works out, I'll be happy with that...and encourage them to take another look at appearance creation for Divinity: Original Sin 3.
One concept I've always been interested in is a game which merges, as much as possible, the ease of play of a video game and the creative power of a tabletop RPG. Not just a virtual tabletop, but something that actually played like a video game, but allowed someone to create and run their own adventures. There have been some attempts throughout the years - Neverwinter Nights, for instance, was a good shot at it, and Sword Coast Legends was a recent...not-quite-as-good shot at it. But nothing's quite gotten there for me - either there was too high of a barrier to entry for the GM for my tastes, or things were easier for the GM but fairly limited in power.
Obviously, that's quite a balancing act. But, fortunately, it hasn't stopped game companies from trying...and that brings me to today's subject, Divinity: Original Sin 2.
The first Divinity: Original Sin is quite a nice game, full of tabletop flavor and with an impressive amount of freedom for a video game - there are constraints, as one would expect since nobody can program for everything, but it definitely feels like you have more approaches to situations than in many other video game RPGs. I've found this particularly interesting in combat, where there seem to be all sorts of interesting tactical options that I can try to take advantage of and usually end up accidentally shocking and stunning my own guy, because I suck at tactical gameplay. The system's pretty brilliant, I'm less so.
Divinity: Original Sin 2 is building on that and adding new tactical options, and expanding the rest of the game besides...but it's also doing one more thing that has me very excited. It's adding a GM mode.
Like the mode in Sword Coast Legends, it appears this one is focused more on the concept of live GMing, rather than building a plot that can be played without a GM like Neverwinter Nights allowed. Not sure if that will be an option too or not. Regardless, the live GMing mode looks very promising in the previews I've seen so far. A few highlights:
- It will be both providing a lot of prebuilt areas and allowing them to be built via some kind of modding package. This was a major early weakness of Sword Coast Legends, which only provided some prebuilts at first (I believe they did eventually add a toolset) - those only work for so long, so it's tough to build a full adventure. The combination of prebuilts and more extensive construction tools should allow a good mix of having what you need to grab at a moment's notice and being able to build something more detailed when needed.
- It looks like it will, like Sword Coast Legends, allow some on-the-fly setup. Not sure on the extent yet, but this is one of the things that game got very right, so I'm pleased to see other companies exploring that idea. If you're used to GMing, you know for a fact that nothing ever goes exactly how you'd plotted it out. Having the ability to add characters, quests, areas, and the like during a session is pretty essential.
- There's a GM override function, so if players want to do some tactic the game doesn't natively allow for, you can improvise and apply effects as you wish. That's just plain cool. One of the weaknesses of video games compared to tabletop gaming has always been that there's constraint over the options players have, to it's great to see that they've planned for ways around that.
- The system itself is turn-based, which...I just always find works better for the tabletop atmosphere. A little more time to think, and more allowance for players to come up with unique tactics that way, too.
- There's a "vignettes" feature that sounds excellent - a way of using images and text (they've compared it to PowerPoint) to convey parts of the story, and allow players to make choices. These sound like a great idea. Sometimes you really don't need to have a full, populated area for part of the story, but you still want to have a little more "pop" to it...this system should allow GMs to present stories in more freeform ways when needed. It looks very pen-and-paper, too.
- This hasn't been confirmed to my knowledge, but Divinity: Original Sin had co-op for two players on a single console - I know the sequel is planning on expanding co-op in general to up to four, but haven't heard if they are going to have two or four players on the same console, or if that can interact with GM mode in any way. It'd be great if we could have the ability to run an adventure for a full party of players on only two computers, one for the GM and the other for the players, but that's probably wishful thinking. Still, it's a good dream.
I'm less enthused by the character creation engine...specifically, for appearance. There's just not that many options at this point for those of us who really get into appearance creation, and I honestly don't know why games based on tabletop roleplaying don't ever go whole hog with character appearance creation the way things like Dynasty Warriors 8: Empires or Dragon's Dogma do, to say nothing of various WWE 2k wrestling games or the like. If any game type should let you truly put the character in your mind on to the screen, it's one with a strong tabletop gaming concept like this, but it never really happens. Here's hoping that they take another look at this at some point, but it seems pretty locked in now. Ah, well. If this GM mode works out, I'll be happy with that...and encourage them to take another look at appearance creation for Divinity: Original Sin 3.
Friday, September 4, 2020
Kriegsspiel: Big Trouble In Little Lardas
Two weeks ago, I participated in a week-long online Kriegsspiel run by Nick Skinner and Richard Clarke of Too Fat Lardies fame. With a total of 13 participants, two umpires and one observer, it was quite an undertaking. Set within a fictional "Imaginations" campaign of the "Lard War II," the players commanded either the forces of the Kingdom of Blue or the Red Republic. As Nick explained in the game:
We confirmed that our organization and equipment was vaguely British. That meant I had three battalions of infantry, each with four companies of four platoons plus a support company. I was also assigned an ambulance company. This seemed a bad omen.
Early in the plans process, I chose to land my initial assault gliders directly on the forts. I figured my best chance was to take the enemy completely by surprise and jump right on top, like at Eben Emael. I had limited resources to get my brigade on the ground. It would take three lifts over the course of two days to get my complete brigade into the battle area. Given my resources at hand, on the initial landings, I would have 20 platoons out of 48 on the ground. Not great odds, I thought. But I had to risk it. Who dares, wins, right?
Plans were set, then changed and changed again as the brigade commanders weighed options and made their cases with the CG and COS for why they should get resources. A feature of Discord that we found handy are voice chat rooms where members can talk via VOIP for planning, rock drills, etc. Blue had two conferences and we found them very beneficial. By the time we had our first conference, we had our plan largely in place and were discussing some of the finer points. The final conference was to make sure everybody had their plans finalized and ask final questions.
The day of battle arrived. As time drew closer for us to climb in our imaginary planes and gliders, top level rooms were locked up and player-to-player communications stopped. We sat at our computers waiting for H-Hour. I received a message that I was on the ground at LZ Baker and could see paras taking heavy fire about a kilometer to the northeast. I could also see and here vicious combat in Fort 2, aka OBJ Grumpy. Then the various communication nets started going live in the form of restricted chat rooms in Discord.
My brigade net room was where I spoke with umpires to get reports from my battalions and request info from them. There was an "on the ground" room for commanders that were up on the division net. Finally there was a division HQ room for those who had established comms with the outside world. Receiving information, parsing it, confirming our own assumptions and then assessing it before putting it up in both the "on the ground" room and Division room was a significant challenge. Luckily, the game was set to last only three hours.
During the game, we were mostly interacting with the umpires and relying on them for information. Issuing orders and requests for information from my imaginary subordinates. I then had to process that info and relay it to my in-game superiors. But only once our in-game communication nets were established! One of the para commanders didn't have comms because his radios got shot up on the DZ. He had to "walk" to where I was and then we could talk to each other and the had to use my "radios" to talk to higher.
Fort 1, OBJ Bashful was taken almost immediately with 30% casualties. Fort 2, OBJ Grumpy, fell only after receiving help from a platoon that had landed on Bashful. Fort 3, OBJ Dopey, was a see-saw battle and I tried mustering forces from Bashful and Grumpy to push it over the edge. Fort 4, OBJ Sleepy, only reported in once their ammo was all expended and the last holdouts were cornered in a bunker and calling "God save the King."
Enemy armored infantry and self-propelled guns had been spotted in the vicinity of Sleepy, so I called for air strikes on the fort with machine gun and cannon only, then follow up with bombs and rockets on the enemy vehicles. Imagine my surprise when I received the report that Sleepy had been destroyed from the air.
In the meantime, I was still trying to get enough forces scratched together to make a difference at Dopey to find it had fallen and was being evacuated, my troops being led away by the enemy. When I asked for clarification if it was Sleepy or Dopey, i was told, "No, it's Dopey, dopey!" Thanks, Rich.
Then the game ended. Luckily, our troops were wholly imaginary and our decisions didn't result in any real casualties. It was an exhilarating, exhausting, madcap, sobering, nervous, mind-blowing experience. I'm planning a podcast with Nick, Richard and the two force commanders. Stay tuned.
I will definitely be looking to do one of these for my J3 group and possibly for my fellow OCS instructors in the near future. Stay tuned for that, as well.
Blue has invaded Red and achieved a breakthrough in the central South. Blue's armies are now pushing Northwards towards the crucial line of the NEMUNAS river and the strategically important city of LARDAS that stands at the confluence of two rivers. If they can push on, they will be threatening the capital city of REDBURG. Red forces though are well organised and aware of the danger. What will happen next?
For the participants, the planning portion was the meat and potatoes of the game. We started out by signing into a website and associated app called Discord. Nick set up a server and we joined it. We were immediately assigned to either the Blue or Red force rooms. From there we received our unit assignments and awaited orders.
The Blue forces, of which I was a member, consisted of an airborne division. We had as players the commanding general, chief of staff, two para brigade commanders, a special reconnaissance squadron commander, a divisional artillery battalion commander and me. I was assigned as the commander of a brigade of glider troops.
The Blue forces, of which I was a member, consisted of an airborne division. We had as players the commanding general, chief of staff, two para brigade commanders, a special reconnaissance squadron commander, a divisional artillery battalion commander and me. I was assigned as the commander of a brigade of glider troops.
 |
| Speaking of gliders. This film and the real events it represents may have provided may have provided some inspiration. |
In the background, Nick was briefing the division commanding general and chief of staff with the division mission. A day or so later, after the CG and COS had some time to digest the mission, we received our unit missions. My mission in particular was to neutralize four forts that protect the southern flank of the city and conduct a follow on mission of clearing the two main routes to the city.
Early in the plans process, I chose to land my initial assault gliders directly on the forts. I figured my best chance was to take the enemy completely by surprise and jump right on top, like at Eben Emael. I had limited resources to get my brigade on the ground. It would take three lifts over the course of two days to get my complete brigade into the battle area. Given my resources at hand, on the initial landings, I would have 20 platoons out of 48 on the ground. Not great odds, I thought. But I had to risk it. Who dares, wins, right?
Plans were set, then changed and changed again as the brigade commanders weighed options and made their cases with the CG and COS for why they should get resources. A feature of Discord that we found handy are voice chat rooms where members can talk via VOIP for planning, rock drills, etc. Blue had two conferences and we found them very beneficial. By the time we had our first conference, we had our plan largely in place and were discussing some of the finer points. The final conference was to make sure everybody had their plans finalized and ask final questions.
The day of battle arrived. As time drew closer for us to climb in our imaginary planes and gliders, top level rooms were locked up and player-to-player communications stopped. We sat at our computers waiting for H-Hour. I received a message that I was on the ground at LZ Baker and could see paras taking heavy fire about a kilometer to the northeast. I could also see and here vicious combat in Fort 2, aka OBJ Grumpy. Then the various communication nets started going live in the form of restricted chat rooms in Discord.
My brigade net room was where I spoke with umpires to get reports from my battalions and request info from them. There was an "on the ground" room for commanders that were up on the division net. Finally there was a division HQ room for those who had established comms with the outside world. Receiving information, parsing it, confirming our own assumptions and then assessing it before putting it up in both the "on the ground" room and Division room was a significant challenge. Luckily, the game was set to last only three hours.
During the game, we were mostly interacting with the umpires and relying on them for information. Issuing orders and requests for information from my imaginary subordinates. I then had to process that info and relay it to my in-game superiors. But only once our in-game communication nets were established! One of the para commanders didn't have comms because his radios got shot up on the DZ. He had to "walk" to where I was and then we could talk to each other and the had to use my "radios" to talk to higher.
Fort 1, OBJ Bashful was taken almost immediately with 30% casualties. Fort 2, OBJ Grumpy, fell only after receiving help from a platoon that had landed on Bashful. Fort 3, OBJ Dopey, was a see-saw battle and I tried mustering forces from Bashful and Grumpy to push it over the edge. Fort 4, OBJ Sleepy, only reported in once their ammo was all expended and the last holdouts were cornered in a bunker and calling "God save the King."
Enemy armored infantry and self-propelled guns had been spotted in the vicinity of Sleepy, so I called for air strikes on the fort with machine gun and cannon only, then follow up with bombs and rockets on the enemy vehicles. Imagine my surprise when I received the report that Sleepy had been destroyed from the air.
In the meantime, I was still trying to get enough forces scratched together to make a difference at Dopey to find it had fallen and was being evacuated, my troops being led away by the enemy. When I asked for clarification if it was Sleepy or Dopey, i was told, "No, it's Dopey, dopey!" Thanks, Rich.
Then the game ended. Luckily, our troops were wholly imaginary and our decisions didn't result in any real casualties. It was an exhilarating, exhausting, madcap, sobering, nervous, mind-blowing experience. I'm planning a podcast with Nick, Richard and the two force commanders. Stay tuned.
I will definitely be looking to do one of these for my J3 group and possibly for my fellow OCS instructors in the near future. Stay tuned for that, as well.
Monday, August 31, 2020
CEH: Gathering Host And Network Information | Scanning
Scanning
It is important that the information-gathering stage be as complete as possible to identify the best location and targets to scan. After the completion of footprinting and information gathering methodologies, scanning is performed.During scanning, the hacker has vision to get information about network an hosts which are connected to that network that can help hackers to determine which type of exploit to use in hacking a system precisely. Information such as an IP addresses, operating system, services, and installed applications.
Scanning is the methodology used to detect the system that are alive and respond on the network or not. Ethical hackers use these type of scanning to identify the IP address of target system. Scanning is also used to determine the availability of the system whether it is connected to the network or not.
Types Of Scanning
| Network Scanning | Identifies IP addresses on a given network or subnet |
| Port Scanning | Determines open, close, filtered and unfiltered ports and services |
| Vulnerability Scanner | Detect the vulnerability on the target system |
Port Scanning
Port scanning is the process of identifying open and available TCP/IP ports on a system. Port-scanning tools enable a hacker to learn about the services available on a given system. Each service or application on a machine is associated with a well-known port number. Port Numbers are divided into three ranges:- Well-Known Ports: 0-1023
- Registered Ports: 1024-49151
- Dynamic Ports: 49152-6553
Network Scanning
Network scanning is performed for the detection of active hosts on a network either you wanna attack them or as a network administrator. Network-scanning tools attempt to identify all the live or responding hosts on the network and their corresponding IP addresses. Hosts are identified by their individual IP addresses.Vulnerability Scanning
This methodology is used to detect vulnerabilities of computer systems on a network. A vulnerability scanner typically identifies the operating system and version number, including applications that are installed. After that the scanner will try to detect vulnerabilities and weakness in the operating system. During the later attack phase, a hacker can exploit those weaknesses in order to gain access to the system. Moreover, the vulnerability scanner can be detected as well, because the scanner must interact over the network with target machine.The CEH Scanning Methodology
As a CEH, you should understand the methodology about scanning presented in the figure below. Because this is the actual need of hackers to perform further attacks after the information about network and hosts which are connected to the network. It detects the vulnerabilities in the system bu which hackers can be accessible to that system by exploitation of that vulnerabilities.More articles
- Hacker Tools 2020
- Tools For Hacker
- Wifi Hacker Tools For Windows
- Pentest Tools Framework
- Pentest Box Tools Download
- Hack App
- Pentest Tools Apk
- How To Make Hacking Tools
- Pentest Tools Subdomain
- Hacker Tools List
- Pentest Tools Port Scanner
- Hacking Tools Name
- Github Hacking Tools
- Hacking Tools Windows
- Hacking Tools Hardware
- Hacker Tools Apk
- Pentest Tools For Ubuntu
- Hacker Tools Windows
- Pentest Tools Tcp Port Scanner
- Usb Pentest Tools
- Hack Tools For Windows
- Hack Tools For Pc
- Hackrf Tools
- Install Pentest Tools Ubuntu
- Hack Tools For Mac
- Hacker Tools Github
- Hack Apps
- Pentest Tools For Windows
- Pentest Automation Tools
- Hack And Tools
- Pentest Tools Windows
- Hack Tool Apk No Root
- Hacking Tools Windows 10
- Nsa Hack Tools Download
- Best Pentesting Tools 2018
- Github Hacking Tools
- Hacking Tools Software
- Computer Hacker
- Hacking Tools Windows
- Hacker Search Tools
- Hacker Tools Mac
- Pentest Tools Url Fuzzer
- Hacker Tools 2019
- Pentest Tools Online
- Pentest Tools Windows
- Github Hacking Tools
- Pentest Tools Free
- Termux Hacking Tools 2019
- Hack Tools 2019
- Hack Rom Tools
- Hacker Tools List
- Hacker Tools Github
- Hacking Tools Name
- Hacking Tools For Games
- Hacking Tools And Software
- Pentest Tools Alternative
- Pentest Tools Review
- Kik Hack Tools
- Hacking App
- Hack App
- Hack Tools
- Pentest Tools Website Vulnerability
- Usb Pentest Tools
- Tools For Hacker
- Pentest Tools For Android
- Hacker Tools List
- Hack Tools Pc
- Nsa Hack Tools Download
- Hacking Tools For Pc
- Hacker Security Tools
- Hacking Tools For Kali Linux
- Hacking Tools Name
- Hacker Tools Apk
- Easy Hack Tools
- Pentest Box Tools Download
- Hacker Tools
- Hacker Tools Mac
- Hacks And Tools
- Hacker Tools For Pc
- Hack Website Online Tool
- Hacking Tools For Windows 7
- Hack Tools Pc
- Hacker Tools Apk
- Hacking Tools Usb
- Ethical Hacker Tools
- Pentest Tools Download
- Pentest Tools Nmap
- Hacking Tools For Beginners
- Tools 4 Hack
- Tools Used For Hacking
- Hacker Tools For Ios
- Hacking Tools Windows 10
- Hacker Tools 2020
- Hacker Tools Github
- Pentest Tools Online
- Pentest Reporting Tools
- Hacking Tools For Mac
- Pentest Tools Open Source
- Hackrf Tools
- Easy Hack Tools
- What Is Hacking Tools
- Hacking Tools For Beginners
- Game Hacking
- Hack Tools
- Hacks And Tools
- Hacking Tools For Games
- Hacking Tools Name
- Hacker Hardware Tools
- Hacking Tools Online
- Hackrf Tools
- Hacking Tools For Kali Linux
- How To Install Pentest Tools In Ubuntu
- New Hack Tools
- Pentest Automation Tools
- Kik Hack Tools
- Hacking Tools
- Hacker
- Hacking Tools For Mac
- Hacking Tools For Pc
- Hacker Tools Free Download
- Hacker Tools Apk
- Hacking Tools Windows
- Beginner Hacker Tools
- Pentest Recon Tools
- Physical Pentest Tools
- Growth Hacker Tools
- Hacking Tools For Beginners
- Hack Apps
- Game Hacking
- Hackers Toolbox
- Hacks And Tools
- Pentest Tools Github
- Bluetooth Hacking Tools Kali
- Bluetooth Hacking Tools Kali
- Nsa Hacker Tools
- Hacker Tools Apk
- Hacker Tools For Windows
- Hacking Tools 2019
- Hack Tools Github
- Best Hacking Tools 2020
- Hack Tools
- Hack Apps
- Hacking Tools For Mac
- Pentest Tools Github
- Pentest Tools Tcp Port Scanner
- Hacker Tools For Ios
- Hacking Tools Hardware
- Pentest Tools Url Fuzzer
- Hack Tools
- Pentest Tools Android
- Hack App
- Hacking Tools For Games
- Hacking Tools Windows 10
- Nsa Hacker Tools
- Hack Rom Tools
- Hack Website Online Tool
- Hacking Tools For Games
- Pentest Tools Android
- Pentest Tools Tcp Port Scanner
- Hacker Tools For Mac
Sunday, August 30, 2020
15 Important Run Commands Every Windows User Should Know
There are several ways to efficiently access the files, folders, and programs in Windows operating system. We can create shortcuts, pin programs to the taskbar, Start menu shortcuts etc. but we can't do it for all programs in many cases. However, the Windows Run Command box is one of the most efficient ways of accessing system programs, folders, and settings.
In this article, I am going to share 15 most important Run commands for Windows users. These commands can make it easier to manage a lot of tasks.
How to open Windows Run command box?
You need to press Win+R (Hold Windows button then Press R)
Important Run Commands Every Windows User Should Know
1. %temp%
This is the fastest way to clear the temporary files from your computer. It can save a lot of space which was being wasted by temporary files.
2. cmd
This command will open the windows DOS command prompt. Windows command prompt is very useful for performing many tasks which are not possible using graphical user interface.
3. MSConfig
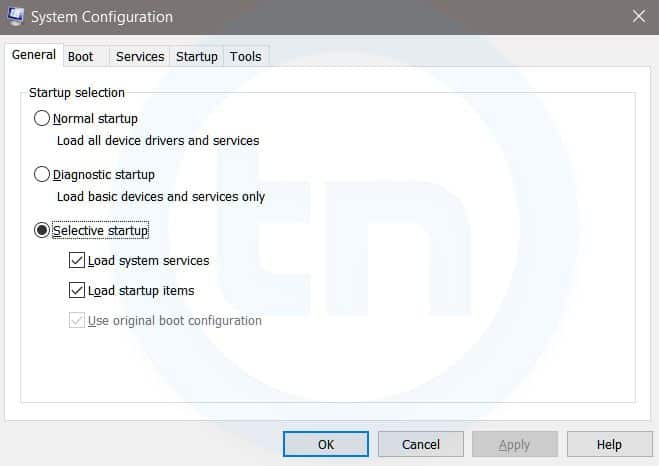
Windows System Configuration
This command will open Windows System Configuration where you can edit different things like the boot options, startup options, services, etc.
4. sysdm.cpl
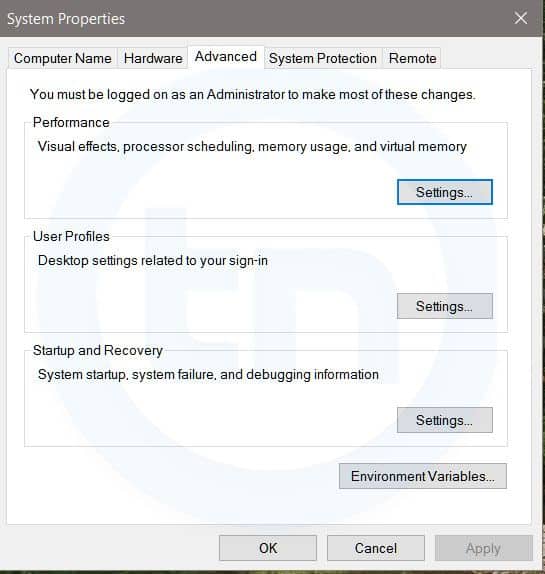
System Properties window
This command will open the System Properties window, Where you can change the system protection and performance related many settings
5. Powershell
Powershell is very similar the command prompt. Just type this command in the Run dialog box, and you will have your PowerShell opened without administrator privileges.
6. perfmon.msc
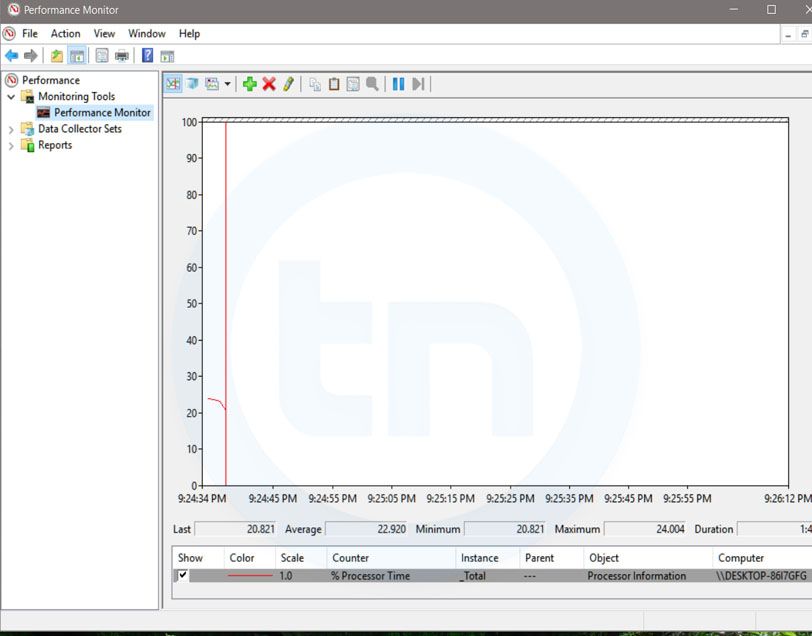
Windows System Performance monitor
This command can be used to monitor the performance of your computer. There are plenty of options for monitoring the system performance
7. regedit
Regedit Run command is used to open the Windows Registry. It is a hierarchical database that hosts all the configurations and settings of Windows operating system, it's users and the installed software.
8. \ (Backslash)
This is one of the lesser known Run commands. Just enter the backslash into the Run dialog box and it will open up the C drive. It is one of the quickest ways to access the C drive.
9. . (Dot)
This is yet another lesser known Run command. When executed, it opens the current user's home folder which hosts all the other local folders like the Downloads, Documents, Desktop, Pictures, etc.
10. .. (Double Dots)
When you execute these two dots in the Run dialog box, it will open up the Users folder which is located directly on the C drive
Also Read; Top 10 Great Gifts For Hackers
11. Control
This command will open the control panel. Control panel is used for managing all the system settings and programs
12. hdwwiz.cpl
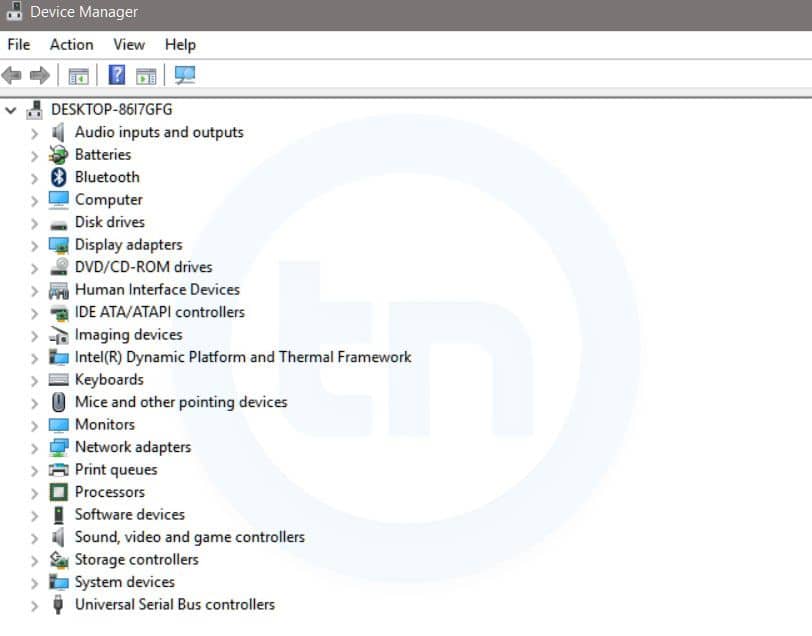
Windows Device Manager
This command is used to open the Device Manager in Windows. You can manage all the device connected internally or externally to your PC.
13. Notepad
The quickest way to open notepad in Windows. Just type this command in Run Box and hit enter.
14. osk
This command will open On-Screen Keyboard on your display monitor. You can easily touch and type or use your mouse for typing.
15. taskmgr
This command will open task manager where you can manage all the processes and programs running on Windows Operating system.
Related word
- Hack Tools Download
- Tools For Hacker
- Computer Hacker
- Github Hacking Tools
- Black Hat Hacker Tools
- Hacking Tools For Mac
- Game Hacking
- How To Make Hacking Tools
- Pentest Tools For Windows
- Hack Tool Apk No Root
- How To Make Hacking Tools
- Hack Tools For Windows
- Pentest Tools Free
- Bluetooth Hacking Tools Kali
- Game Hacking
- Hacking Tools Hardware
- Pentest Tools Tcp Port Scanner
- Black Hat Hacker Tools
- Game Hacking
- Pentest Tools Framework
- Nsa Hacker Tools
- New Hacker Tools
- Hack And Tools
- Ethical Hacker Tools
- Hack Rom Tools
- Blackhat Hacker Tools
- Hacks And Tools
- Hacking Tools For Kali Linux
- Hack Tools For Mac
- Pentest Tools Nmap
- Hacking Tools Free Download
- Hacker Tools Github
- Termux Hacking Tools 2019
- Computer Hacker
- Pentest Tools Website
- Wifi Hacker Tools For Windows
- Pentest Tools
- Hack Tools For Mac
- Pentest Tools For Windows
- Hacking Tools Usb
- Hack And Tools
- Beginner Hacker Tools
- Usb Pentest Tools
- Ethical Hacker Tools
- Hacking Tools For Mac
- Hacker Tools Hardware
- Hacking Tools For Beginners
- Hacking Tools Online
- How To Install Pentest Tools In Ubuntu
- Pentest Tools List
- Hacking Tools Github
- Kik Hack Tools
- Hacker Tools Hardware
- Hacking Tools For Windows 7
- Hack Tools Github
- Hacking Tools 2019
- Tools 4 Hack
- Hacker Tools For Mac
- Hack Tools For Mac
- Android Hack Tools Github
- Hacking Tools Windows 10
- Hacking Tools
- Pentest Tools Nmap
- Nsa Hack Tools Download
- Tools 4 Hack
- Hack Apps
- Hacking Tools Windows 10
- Hacking Tools Hardware
- How To Make Hacking Tools
- Hacker Tools For Windows
- Hacking Tools Windows 10
- Hacking Tools Free Download
- Hacker Tools Mac
- Hack Tools For Mac
- Hacker Tools Linux
- Pentest Tools Website
- Hack Tools For Windows
- Hacker Tools For Pc
- Hacking Tools Mac
- What Is Hacking Tools
- Hack Tools
- Best Hacking Tools 2020
- Hacks And Tools
- Hacking Tools For Windows
- Hacker
- Hack Tools For Games
- Pentest Tools Subdomain
- Hack Tools Pc
- Pentest Automation Tools
- Termux Hacking Tools 2019
- New Hacker Tools
- Pentest Reporting Tools
- Hack Tools Github
- Hacker Tools 2019
- Game Hacking
- Hacking Tools And Software
- What Are Hacking Tools
- Hacker Tools Hardware
- Hack Tools Online
- Pentest Tools Framework
- Hack Tools
- Hacking Tools Pc
- Hacker Tools Free
- Blackhat Hacker Tools
- Hacking Tools Windows 10
- Hacking Tools Software
- Hacking Tools Hardware
- Hacker Tools Windows
- Hacking Tools Name
- Pentest Tools Nmap
- Hack Tools 2019
- Tools 4 Hack
- Wifi Hacker Tools For Windows
- Pentest Tools Linux
- Hacking Tools For Windows Free Download
- Install Pentest Tools Ubuntu
- Hacking Apps
- Hak5 Tools
- Hack Tools Github
- Hack Tools Mac
- Hacker Tools Github
- Hacker Tools Windows
- Best Hacking Tools 2020
- Hack And Tools
- Pentest Tools Port Scanner
- Hacking Tools Kit
- Hack Tools Pc
- Hack Tools For Ubuntu
- Hacking Tools Online
- Hack Website Online Tool
- Hacking Tools Mac
- Hacker Tools Apk Download
- Hacker Tools 2019
- Hacker Tools
- Pentest Tools Bluekeep
- Pentest Tools Framework
- Computer Hacker
- Hacker Tools Windows
- Hak5 Tools
- Hacker Tools Windows
- Hacker Tools Software
- Hacker Techniques Tools And Incident Handling
- Hackers Toolbox
- Pentest Tools For Windows
- New Hack Tools
- Pentest Tools Website
- Hack Tools For Pc
- Hackrf Tools
- Hacking Tools For Windows
- Pentest Tools Free
- Hacking Apps
- What Are Hacking Tools
- Hacker Tools For Ios
- Hacker Tools Online
- Pentest Tools Nmap
- Nsa Hacker Tools
- Hacking Tools Usb
- Pentest Tools For Ubuntu
- Hak5 Tools
- Nsa Hack Tools Download
- Hack Tools
- Usb Pentest Tools
- Hacker Tools Mac
- Free Pentest Tools For Windows
- Pentest Tools Subdomain
- Hacking Tools Windows
- Pentest Tools Framework
- Pentest Tools Android
- Pentest Tools Github
- Hacking Tools Online
- Beginner Hacker Tools
- Nsa Hack Tools Download
- Hacker Tools Apk
- Best Hacking Tools 2019
- Hacking Tools For Pc
Subscribe to:
Comments (Atom)
Blog Archive
-
►
2025
(47)
- ► 06/29 - 07/06 (2)
- ► 06/01 - 06/08 (1)
- ► 05/25 - 06/01 (1)
- ► 04/27 - 05/04 (1)
- ► 04/13 - 04/20 (2)
- ► 03/23 - 03/30 (6)
- ► 03/16 - 03/23 (1)
- ► 02/16 - 02/23 (2)
- ► 02/09 - 02/16 (2)
- ► 02/02 - 02/09 (1)
- ► 01/26 - 02/02 (2)
- ► 01/19 - 01/26 (3)
- ► 01/12 - 01/19 (5)
- ► 01/05 - 01/12 (18)
-
►
2024
(53)
- ► 12/22 - 12/29 (1)
- ► 11/10 - 11/17 (1)
- ► 09/22 - 09/29 (1)
- ► 03/03 - 03/10 (1)
- ► 02/04 - 02/11 (2)
- ► 01/28 - 02/04 (9)
- ► 01/21 - 01/28 (27)
- ► 01/14 - 01/21 (11)
-
►
2023
(62)
- ► 12/31 - 01/07 (1)
- ► 12/03 - 12/10 (1)
- ► 09/24 - 10/01 (1)
- ► 08/13 - 08/20 (1)
- ► 08/06 - 08/13 (2)
- ► 07/30 - 08/06 (3)
- ► 07/23 - 07/30 (2)
- ► 07/09 - 07/16 (1)
- ► 06/11 - 06/18 (5)
- ► 06/04 - 06/11 (10)
- ► 05/28 - 06/04 (23)
- ► 05/21 - 05/28 (12)
-
►
2022
(1)
- ► 07/31 - 08/07 (1)
-
▼
2020
(357)
- ► 09/06 - 09/13 (2)
- ► 08/30 - 09/06 (5)
- ► 08/23 - 08/30 (19)
- ► 08/16 - 08/23 (26)
- ► 08/09 - 08/16 (23)
- ► 08/02 - 08/09 (23)
- ► 07/26 - 08/02 (23)
- ► 07/19 - 07/26 (23)
- ► 07/12 - 07/19 (23)
- ► 07/05 - 07/12 (23)
- ► 06/28 - 07/05 (15)
- ► 06/07 - 06/14 (15)
- ► 05/31 - 06/07 (12)
- ► 05/17 - 05/24 (22)
- ► 05/10 - 05/17 (16)
- ► 05/03 - 05/10 (7)
- ► 04/26 - 05/03 (7)
- ► 04/19 - 04/26 (19)
- ► 04/12 - 04/19 (26)
- ► 04/05 - 04/12 (2)
- ► 03/22 - 03/29 (4)
- ► 03/15 - 03/22 (6)
- ► 03/01 - 03/08 (5)
- ► 02/23 - 03/01 (2)
- ► 02/16 - 02/23 (6)
- ► 02/09 - 02/16 (1)
-
►
2019
(1072)
- ► 12/01 - 12/08 (12)
- ► 11/24 - 12/01 (38)
- ► 11/17 - 11/24 (24)
- ► 09/15 - 09/22 (54)
- ► 09/08 - 09/15 (82)
- ► 09/01 - 09/08 (52)
- ► 08/25 - 09/01 (56)
- ► 08/18 - 08/25 (68)
- ► 08/11 - 08/18 (66)
- ► 08/04 - 08/11 (62)
- ► 07/28 - 08/04 (61)
- ► 07/21 - 07/28 (64)
- ► 07/14 - 07/21 (71)
- ► 07/07 - 07/14 (65)
- ► 06/30 - 07/07 (60)
- ► 06/23 - 06/30 (37)
- ► 06/16 - 06/23 (26)
- ► 06/09 - 06/16 (52)
- ► 06/02 - 06/09 (48)
- ► 05/26 - 06/02 (50)
- ► 05/19 - 05/26 (9)
- ► 03/31 - 04/07 (3)
- ► 03/24 - 03/31 (11)
- ► 03/17 - 03/24 (1)
-
►
2018
(2)
- ► 06/24 - 07/01 (2)
-
►
2015
(1)
- ► 03/15 - 03/22 (1)
-
►
2012
(3)
- ► 03/11 - 03/18 (1)
- ► 01/29 - 02/05 (1)
- ► 01/08 - 01/15 (1)
-
►
2011
(38)
- ► 10/23 - 10/30 (1)
- ► 10/16 - 10/23 (1)
- ► 10/09 - 10/16 (1)
- ► 10/02 - 10/09 (4)
- ► 09/25 - 10/02 (2)
- ► 09/18 - 09/25 (2)
- ► 05/29 - 06/05 (1)
- ► 05/22 - 05/29 (1)
- ► 05/15 - 05/22 (2)
- ► 05/08 - 05/15 (2)
- ► 04/10 - 04/17 (2)
- ► 04/03 - 04/10 (1)
- ► 03/27 - 04/03 (1)
- ► 03/20 - 03/27 (3)
- ► 03/06 - 03/13 (2)
- ► 02/27 - 03/06 (3)
- ► 02/13 - 02/20 (1)
- ► 02/06 - 02/13 (1)
- ► 01/23 - 01/30 (1)
- ► 01/16 - 01/23 (1)
- ► 01/09 - 01/16 (3)
- ► 01/02 - 01/09 (2)
-
►
2010
(61)
- ► 12/05 - 12/12 (2)
- ► 11/28 - 12/05 (2)
- ► 11/14 - 11/21 (2)
- ► 11/07 - 11/14 (3)
- ► 10/31 - 11/07 (5)
- ► 10/24 - 10/31 (5)
- ► 10/17 - 10/24 (4)
- ► 05/16 - 05/23 (1)
- ► 05/02 - 05/09 (2)
- ► 04/18 - 04/25 (3)
- ► 04/11 - 04/18 (2)
- ► 03/21 - 03/28 (4)
- ► 03/14 - 03/21 (3)
- ► 03/07 - 03/14 (4)
- ► 02/28 - 03/07 (1)
- ► 02/21 - 02/28 (2)
- ► 02/07 - 02/14 (2)
- ► 01/31 - 02/07 (2)
- ► 01/24 - 01/31 (3)
- ► 01/17 - 01/24 (2)
- ► 01/10 - 01/17 (3)
- ► 01/03 - 01/10 (4)
-
►
2009
(3)
- ► 12/13 - 12/20 (3)


















